Applies To:
Show Versions
BIG-IP AAM
- 11.6.5, 11.6.4, 11.6.3, 11.6.2, 11.6.1
BIG-IP APM
- 11.6.5, 11.6.4, 11.6.3, 11.6.2, 11.6.1
BIG-IP GTM
- 11.6.5, 11.6.4, 11.6.3, 11.6.2, 11.6.1
BIG-IP Analytics
- 11.6.5, 11.6.4, 11.6.3, 11.6.2, 11.6.1
BIG-IP Link Controller
- 11.6.5, 11.6.4, 11.6.3, 11.6.2, 11.6.1
BIG-IP LTM
- 11.6.5, 11.6.4, 11.6.3, 11.6.2, 11.6.1
BIG-IP PEM
- 11.6.5, 11.6.4, 11.6.3, 11.6.2, 11.6.1
BIG-IP AFM
- 11.6.5, 11.6.4, 11.6.3, 11.6.2, 11.6.1
BIG-IP ASM
- 11.6.5, 11.6.4, 11.6.3, 11.6.2, 11.6.1
Configuring IPsec in Tunnel Mode between Two BIG-IP Systems
Overview: Configuring IPsec between two BIG-IP systems
You can configure an IPsec tunnel when you want to use a protocol other than SSL to secure traffic that traverses a wide area network (WAN), from one BIG-IP ®system to another. By following this procedure, you can configure an IKE peer to negotiate Phase 1 Internet Security Association and Key Management Protocol (ISAKMP) security associations for the secure channel between two systems. You can also configure a custom traffic selector and a custom IPsec policy that use this secure channel to generate IPsec Tunnel mode (Phase 2) security associations (SAs).
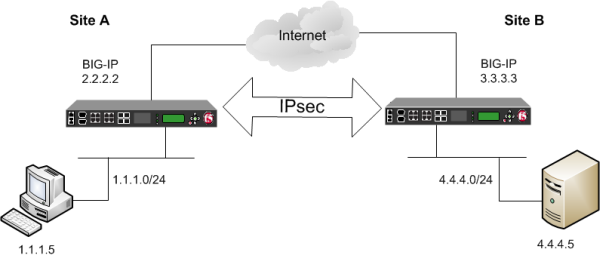
Example of an IPsec deployment
About negotiation of security associations
The way to dynamically negotiate security associations is to configure the Internet Key Exchange (IKE) protocol, which is included in the IPsec protocol suite. When you configure the IKE protocol, two IPsec tunnel endpoints (IKE peers) open a secure channel using an ISAKMP security association (ISAKMP-SA) to initially negotiate the exchange of peer-to-peer authentication data. This exchange is known as Phase 1 negotiation.
After Phase 1 is complete and the secure channel is established, Phase 2 negotiation begins, in which the IKE peers dynamically negotiate the authentication and encryption algorithms to use to secure the payload. Without IKE, the system cannot dynamically negotiate these security algorithms.
About IPsec Tunnel mode
Tunnel mode causes the IPsec protocol to encrypt the entire packet (the payload plus the IP header). This encrypted packet is then included as the payload in another outer packet with a new header. Traffic sent in this mode is more secure than traffic sent in Transport mode, because the original IP header is encrypted along with the original payload.
About BIG-IP components of the IPsec protocol suite
The IPsec protocol suite on the BIG-IP® system consists of these configuration components:
- IKE peers
- An IKE peer is a configuration object of the IPsec protocol suite that
represents a BIG-IP system on each side of the IPsec tunnel. IKE peers allow two systems to
authenticate each other (known as IKE Phase 1). The BIG-IP system supports two versions of the
IKE protocol: Version 1 (IKEv1) and Version 2 (IKEv2). The BIG-IP system includes the default
IKE peer, named anonymous, which is configured to use Version 1.Note: The BIG-IP system currently supports IKEv2 only in Tunnel mode, and does not support IPComp or NAT-T with IKEv2.
- IPsec policies
- An IPsec policy is a set of information that defines the specific IPsec protocol to use (ESP or AH), and the mode (Transport, Tunnel, or iSession). For Tunnel mode, the policy also specifies the endpoints for the tunnel, and for IKE Phase 2 negotiation, the policy specifies the security parameters to be used in that negotiation. The way that you configure the IPsec policy determines the way that the BIG-IP system manipulates the IP headers in the packets. The BIG-IP system includes two default IPsec policies, named default-ipsec-policy and default-ipsec-policy-isession. A common configuration includes a bidirectional policy on each BIG-IP system.
- Traffic selectors
- A traffic selector is a packet filter that defines what traffic should be handled by a IPsec policy. You define the traffic by source and destination IP addresses and port numbers. A common configuration includes a bidirectional traffic selector on each BIG-IP system.
About IP Payload Compression Protocol (IPComp)
IP Payload Compression Protocol (IPComp) is a protocol that reduces the size of IP payloads by compressing IP datagrams before fragmenting or encrypting the traffic. IPComp is typically used to improve encryption and decryption performance, thus increasing bandwidth utilization. Using an IPsec ESP tunnel can result in packet fragmentation, because the protocol adds a significant number of bytes to a packet. The additional bytes can push the packet over the maximum size allowed on the outbound link. Using compression is one way to mitigate fragmentation. IPComp is an option when you create a custom IPsec policy.
Task summary
You can configure the IPsec and IKE protocols to secure traffic that traverses a wide area network (WAN), such as from one data center to another.
Before you begin configuring IPsec and IKE, verify that these modules, system objects, and connectivity exist on the BIG-IP systems in both the local and remote locations:
- BIG-IP Local Traffic Manager™
- This module directs traffic securely and efficiently to the appropriate destination on a network.
- Self IP address
- Each BIG-IP system must have at least one self IP address, to be used in specifying the ends of the IPsec tunnel.
- The default VLANs
- These VLANs are named external and internal.
- BIG-IP connectivity
- Verify the connectivity between the client or server and its BIG-IP device, and between each BIG-IP device and its gateway. For example, you can use ping to test this connectivity.
Task list
Creating a forwarding virtual server for IPsec
Creating a custom IPsec policy
You create a custom IPsec policy when you want to use a policy other than the default IPsec policy (default-ipsec-policy or default-ipsec-policy-isession). A typical reason for creating a custom IPsec policy is to configure IPsec to operate in Tunnel rather than Transport mode. Another reason is to add payload compression before encryption. If you are using IKEv2, you must create a custom IPsec policy to specify in the traffic selector you create.
Creating a bidirectional IPsec traffic selector
Creating an IKE peer
The IKE peer object identifies to the system you are configuring the other BIG-IP system with which it communicates during Phase 1 negotiations. The IKE peer object also specifies the specific algorithms and credentials to be used for Phase 1 negotiation.
Verifying IPsec connectivity for Tunnel mode
After you have configured an IPsec tunnel and before you configure additional functionality, you can verify that the tunnel is passing traffic.
Implementation result
You now have an IPsec tunnel for securing traffic that traverses the WAN, from one BIG-IP system to another.





