Manual Chapter :
Common elements for
cipher rules and groups
Applies To:
Show Versions
BIG-IP AAM
- 15.0.1, 15.0.0
BIG-IP APM
- 15.0.1, 15.0.0
BIG-IP Link Controller
- 15.0.1, 15.0.0
BIG-IP Analytics
- 15.0.1, 15.0.0
BIG-IP LTM
- 15.0.1, 15.0.0
BIG-IP AFM
- 15.0.1, 15.0.0
BIG-IP PEM
- 15.0.1, 15.0.0
BIG-IP DNS
- 15.0.1, 15.0.0
BIG-IP ASM
- 15.0.1, 15.0.0
Common elements for
cipher rules and groups
- On the Main tab, click .The screen displays a list of pre-built cipher rules.
- ClickCreate.
- In theNamefield, type a name for the cipher rule.Never include the prefixf5-in a cipher rule name. This prefix is reserved for pre-built cipher rules only.For example:
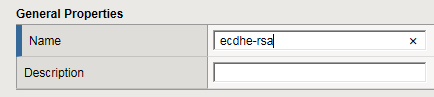
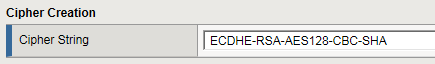
- In theCipher Suitesfield, type one or more cipher suites.For example:
- On the Main tab, click .The screen displays a list of pre-built cipher groups.
- In theNamefield, type a name for the cipher group.Never include the prefixf5-in a cipher rule name. This prefix is reserved for pre-built cipher groups only.
- If you created any custom rules, then in the Cipher Creation area of the screen in theAvailable Cipher Ruleslist, verify that the custom rules appear in the list.
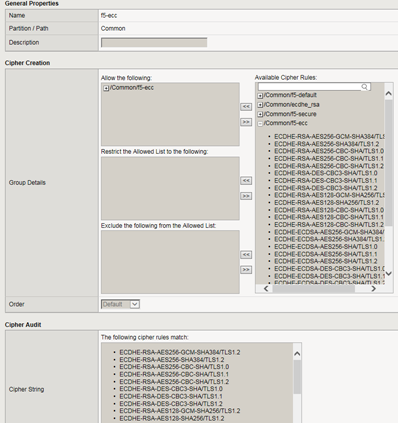
- For each cipher rule in theAvailable Cipher Ruleslist, click the plus sign to view the cipher suites included in the rule.For example, this shows the cipher suites included in the pre-built cipher rule named/Common/f5-ecc.
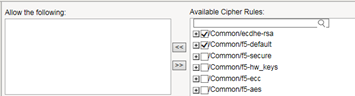
- In theAvailable Cipher Ruleslist, select the boxes for the cipher rules you want to allow for negotiating security for SSL connections.We strongly recommend that you select the cipher rule/Common/f5-default, and for added security, select other cipher rules, too.Here's an example of a list of available cipher rules that you might see within a cipher group. Notice that we've selected both a pre-built cipher rule and a custom cipher rule:
- In theGroup Detailssetting, move the selected cipher rules to theAllow the followingbox.Here we see that we're instructing the BIG-IP system to allow, during security negotiation, the cipher suites contained in the selected cipher rules:
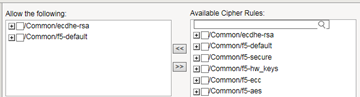
- Again from theAvailable Cipher Ruleslist, select the boxes for the cipher rules you want to restrict the allowed cipher rules to when negotiating security for SSL connections.
- Move the selected cipher rules to theRestrict the Allowed list to the followingbox.
- If you want to exclude any cipher rules from the allowed list, then from theAvailable Cipher Ruleslist, select the boxes for the rules you want to exclude.
- Move the selected cipher rules to theExclude the following from the Allowed listbox.
- From theOrderlist, select the order that you want the BIG-IP system to use when negotiating SSL connections.The choices are:Default,Speed,Strength,FIPS, andHardware.
- In theCryptographic Parametersbox, view the cipher suites that the BIG-IP system will use to construct the final cipher string, based on the selections you made in the previous steps.
- ClickFinished.
- ClickFinished.
- ClickCancel.





