Applies To:
Show Versions
Manipulating HTTPS Traffic by Using a Third-Party Device
Overview: Manipulating HTTPS traffic by using a third-party device
You can configure a BIG-IP® device to manage HTTPS traffic by using a third-party device that can intercept and modify the traffic, as necessary. This configuration provides SSL decryption, manipulation, and re-encryption while appearing relatively transparent at layer 2.
The basic process used in this configuration is as follows:
- A client sends an HTTPS request to a server by means of the BIG-IP device.
- The BIG-IP device intercepts the request, decrypts it, and forwards the request as cleartext to the inspection device.
- The inspection device receives and, as necessary, modifies the cleartext request.
- The inspection device forwards the cleartext request to the server by means of the BIG-IP device.
- The BIG-IP device re-encrypts the cleartext request and sends the ciphertext request to the server.
- The server sends a response to the client by means of the BIG-IP device.
- The BIG-IP device receives the response, decrypts it, and forwards the response as cleartext to the inspection device.
- The inspection device receives and, as necessary, modifies the cleartext response.
- The inspection device forwards the cleartext response to the client by means of the BIG-IP device.
- The BIG-IP device re-encrypts the cleartext response and sends the ciphertext response to the client.
The following illustration shows an example of a BIG-IP device that manages HTTPS traffic modified by a third-party device.
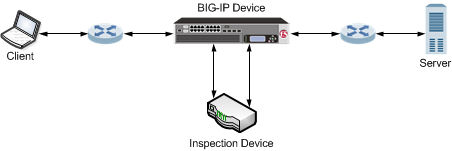
An example configuration of a BIG-IP device managing HTTPS traffic modified by a third-party device.
Task summary for manipulating HTTPS traffic thru third-party devices
Complete these tasks to configure a BIG-IP® device to manage HTTPS traffic by using a third-party device that can intercept and modify the traffic, as necessary.
Creating a VLAN
Creating a custom Client SSL profile
- Authenticating and decrypting ingress client-side SSL traffic
- Re-encrypting egress client-side traffic
Creating a custom Server SSL profile
Task summary for manipulating HTTPS traffic thru third-party devices
Complete these tasks to configure a BIG-IP® device to manage HTTPS traffic by using a third-party device that can intercept and modify the traffic, as necessary.





